- Integrations
- AWS Cognito
Integrations
AWS Cognito
This tutorial demonstrates how to integrate Criipto Verify with AWS Cognito
AWS Cognito basics
Your AWS Cognito user pool must be configured without email as an required attribute.
Make sure you have configured a Amazon Cognito domain for your AWS Cognito user pool (in this example we have picked https://criipto-samples.auth.us-east-1.amazoncognito.com)
Register your Criipto Application
- Login to you Criipto Verify account - https://dashboard.criipto.com/applications/add
- Navigate to Applications
- Click the "Add login application" button
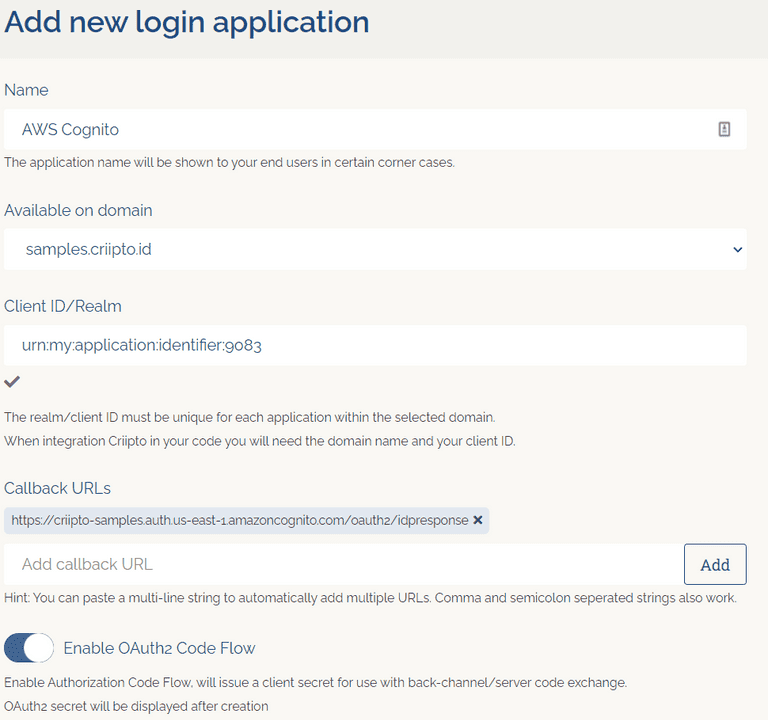
- Enter application name (in this example we used "AWS Cognito" and select a domain)
- Register the callback URL for your AWS Cognito Domain (
https://<your-user-pool-domain>/oauth2/idpresponse) - Enable OAuth2 Code Flow
- Create application and make a note of your client id and client secret
- Modify your "User info response strategy" to "plainJson" and save your application.
AWS Cognito provider setup
- Go to your existing or newly created AWS Cognito User Pool.
- Go to Federation > Identity Providers
- Click OpenID Connect
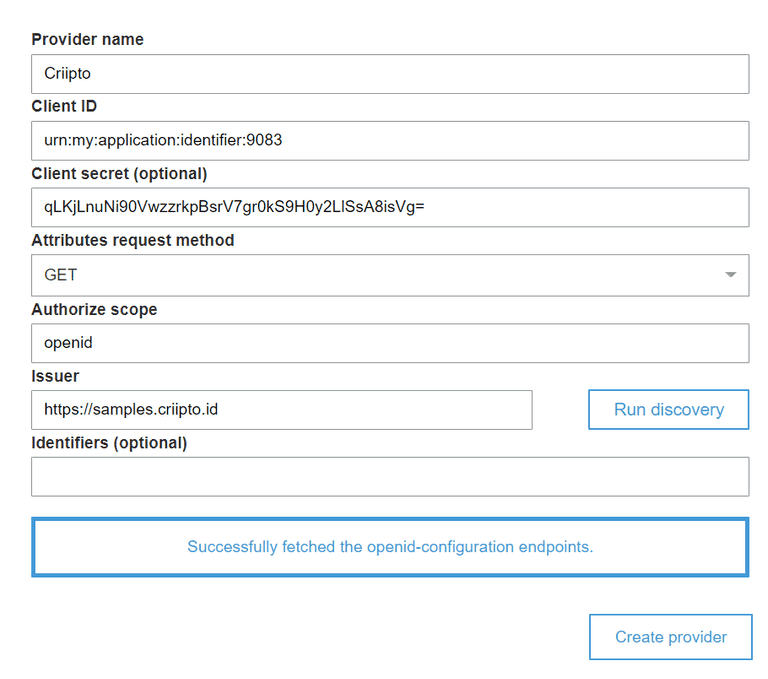
- Enter a provider name (in this example we used "Criipto")
- Enter your Criipto Application client id in the "Client ID" field
- Enter your Criipto Application client secret in the "Client Secret" field
- Enter "openid" in "Authorize scope" field
- Enter
https://{{YOUR_CRIIPTO_DOMAIN}}in the "Issuer" field - Click "Run discovery"
- Click "Create provider"
AWS Cognito application setup
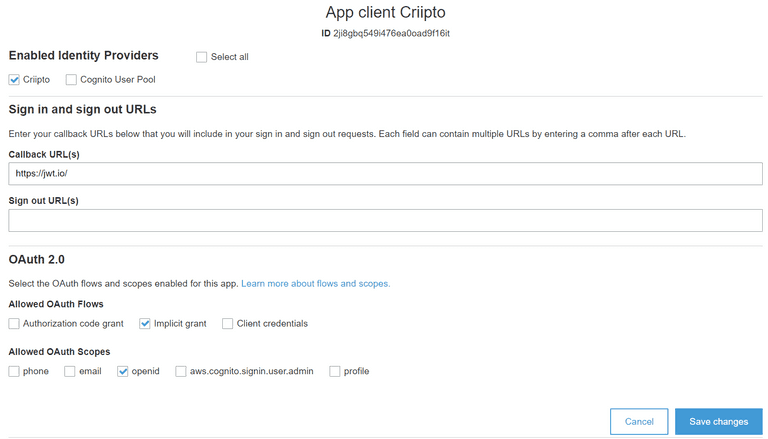
- Create a new Cognito app client or use an existing one.
- Go to "App client settings" and find your Cognito app client.
- Mark "Criipto" (or whatever provider name you picked for your AWS Cognito provider)
- Add a callback URL to your application if you have not already
- Setup OAuth2 scopes
- Click "Save changes"
Perform a login
Launch the hosted UI for your AWS Cognito domain/client or perform an authorize request.
Common errors
invalid token_type in idp oauth response: Make sure "User info response strategy" is configured as "plainJson"