- Integrations
- Auth0
Integrations
Auth0
This tutorial demonstrates how to integrate Idura Verify with Auth0.
This tutorial demonstrates how to integrate Idura Verify with Auth0. The following steps are required to complete your first login:
- Register your Auth0 tenant in Idura Verify
- Configure OAuth2 Code Flow
- Create Auth0 connections
- Integrate your application with Auth0
In the following, you'll first configure Idura Verify, then Auth0, and finally complete the Idura Verify configuration with the information you get from Auth0. Once everything's configured, you can test your integration from Auth0.
Register your Auth0 tenant in Idura Verify
First, create a new application for your Auth0 tenant in Idura Verify. This is done via the Idura Dashboard.
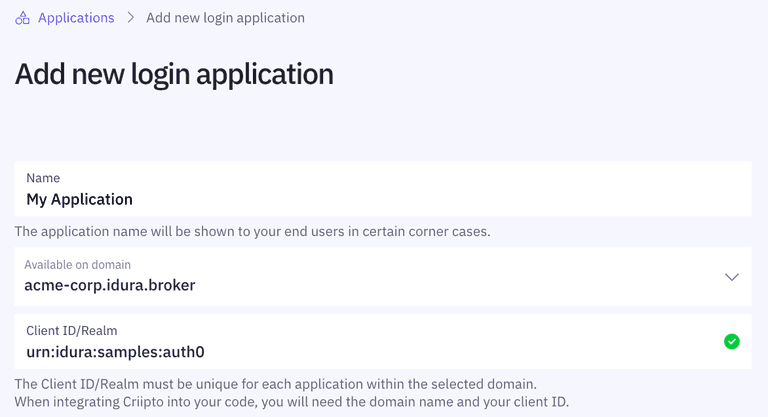
Once the application is created, you'll need some of its details for configuring Auth0 to communicate with Idura Verify. Gather the following information from the application settings:
- Client ID to identify your Auth0 tenant to Idura Verify. We chose
urn:idura:samples:auth0for this example. - Domain on which you will be communicating with Idura Verify. If your company name is Acme Corp, it could be, for example,
acme-corp.idura.broker. - Client secret is needed if you choose the back-channel approach. The secret is generated when you configure OAuth2 Code Flow for your application.
Configure OAuth2 Code Flow
If you are registering a new application, please save the initial configuration first.
After saving, you can configure the OAuth2 Code Flow for this application by following the three steps:
- Go to the OpenID Connect section of your Application settings and Enable OAuth2 Code Flow.
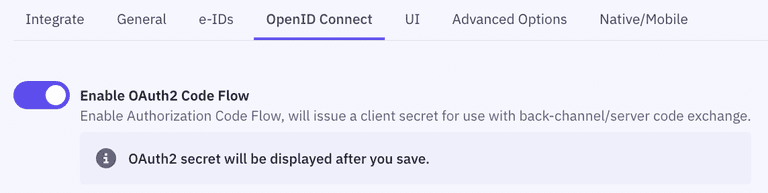
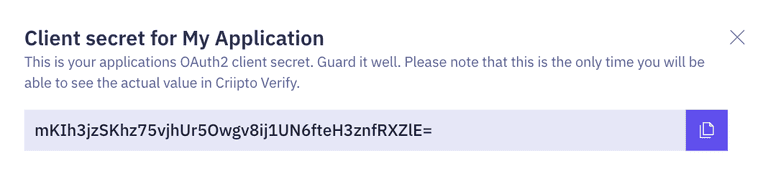
- Copy the generated client secret. Note that this is the only time you will be shown the actual value of the client secret. Idura only stores this as a hashed value, which means you cannot retrieve the value once it has been generated and stored.
- Set the user info response strategy to
plainJsonto enable retrieval of plain JSON user information from the/oauth2/userinfoendpoint.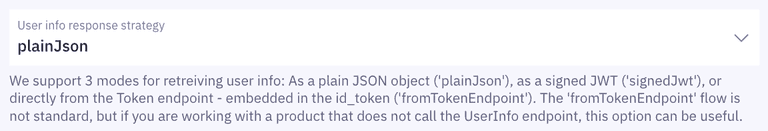 Note that some libraries do not support the final
Note that some libraries do not support the final userinforequest. In those cases, you will need to fetch the user data directly from thetokenendpoint as opposed to theuserinfoendpoint. You can do this by choosingfromTokenEndpointas aUser info response strategy.
Idura Verify supports four modes for retrieving user information:
- Plain JSON object (
plainJson): User information is returned from theuserinfoendpoint as a standard JSON object. - Signed JWT (
signedJwt): User information is returned from theuserinfoendpoint as a digitally signed JSON Web Token. - Signed and encrypted JWT (
signedAndEncryptedJwt): User information is returned from theuserinfoendpoint as a signed and encrypted JSON Web Encryption(JWE) object. - Directly from the
tokenendpoint, embedded in theid_token(fromTokenEndpoint). ThefromTokenEndpointflow is not standard, but can be useful if you are working with a product that does not call theuserinfoendpoint.
Create Auth0 connections
You can leverage either an Enterprise Connection, or a Custom Social Connection to connect Idura Verify with Auth0.
Login-method specific endpoints
To integrate Idura Verify with Auth0, you create an Auth0 OpenID Connect(OIDC) connection to communicate with Idura Verify. Because Auth0 will not pass the acr_values to Idura Verify, you will have to create a new connection for every eID option that you intend to use. (acr_values is a parameter in the /authorize request to Idura Verify needed to specify which kind of eID is requested).
For those cases, you can leverage our login-method specific metadata endpoints (for Enterprise Connections) and authorize URLs (for Custom Social Connections). Each of these contain an embedded and base64-encoded variant of the "raw" value normally supplied in the acr_values.
Syntax:
- Issuer metadata endpoint:
https://yourdomain.idura.broker/BASE64(acr_values)/.well-known/openid-configuration - Authorize URL:
https://yourdomain.idura.broker/BASE64(acr_values)/oauth2/authorize
For example, the acr_values of Norwegian BankID login method is urn:grn:authn:no:bankid. This translates to dXJuOmdybjphdXRobjpubzpiYW5raWQ= in base64 (UTF-8 charset), so the syntax will be:
- Issuer metadata endpoint:
https://yourdomain.idura.broker/dXJuOmdybjphdXRobjpubzpiYW5raWQ=/.well-known/openid-configuration - Authorize URL:
https://yourdomain.idura.broker/dXJuOmdybjphdXRobjpubzpiYW5raWQ=/oauth2/authorize
Choose the specific login method
Below is a list of supported login methods with the corresponding base64 encoded acr_values. Choose the ones you intend to use.
| Login method | acr_values | base64 encoded |
|---|---|---|
| Norwegian BankID | ||
| Mobile or Web (user choice): | urn:grn:authn:no:bankid | dXJuOmdybjphdXRobjpubzpiYW5raWQ= |
| BankID Biometrics (level substantial): | urn:grn:authn:no:bankid:substantial | dXJuOmdybjphdXRobjpubzpiYW5raWQ6c3Vic3RhbnRpYWw= |
| Norwegian Vipps Login | ||
| Login with Vipps app: | urn:grn:authn:no:vipps | dXJuOmdybjphdXRobjpubzp2aXBwcw== |
| Swedish BankID | ||
| All options (user chooses): | urn:grn:authn:se:bankid | dXJuOmdybjphdXRobjpzZTpiYW5raWQ= |
| Same device: | urn:grn:authn:se:bankid:same-device | dXJuOmdybjphdXRobjpzZTpiYW5raWQ6c2FtZS1kZXZpY2U= |
| Another device (aka mobile): | urn:grn:authn:se:bankid:another-device | dXJuOmdybjphdXRobjpzZTpiYW5raWQ6YW5vdGhlci1kZXZpY2U= |
| QR code: | urn:grn:authn:se:bankid:another-device:qr | dXJuOmdybjphdXRobjpzZTpiYW5raWQ6YW5vdGhlci1kZXZpY2U6cXI= |
| Danish MitID | ||
| Level low: | urn:grn:authn:dk:mitid:low | dXJuOmdybjphdXRobjpkazptaXRpZDpsb3c= |
| Level substantial: | urn:grn:authn:dk:mitid:substantial | dXJuOmdybjphdXRobjpkazptaXRpZDpzdWJzdGFudGlhbA== |
| MitID Erhverv (MitID Business): | urn:grn:authn:dk:mitid:business | dXJuOmdybjphdXRobjpkazptaXRpZDpidXNpbmVzcw== |
| Finnish Trust Network | ||
| BankID: | urn:grn:authn:fi:bankid | dXJuOmdybjphdXRobjpmaTpiYW5raWQ= |
| Mobile certificate (Mobiilivarmenne): | urn:grn:authn:fi:mobile-id | dXJuOmdybjphdXRobjpmaTptb2JpbGUtaWQ= |
| Both of the above: | urn:grn:authn:fi:all | dXJuOmdybjphdXRobjpmaTphbGw= |
Enterprise Connection
You can connect Auth0 to Idura Verify by creating an OIDC Enterprise Connection. You create an OIDC connection for every login method you intend to use.
Create the OIDC connection(s)
- Go to Auth0 dashboard for your tenant and under Authentication choose Enterprise.
- Select OpenID Connect and create a new connection.
- Enter Connection name.
- Under Issuer URL enter the login-method specific URL, as described above.
- Under Client ID enter the Client ID/Realm from your Idura Verify application.
- Copy the Callback URL generated by Auth0. In your Idura dashboard, open the General tab of your application settings and paste this URL into the Redirect URLs field.
- Back in the Auth0 dashboard, create a connection by clicking Create.
- After the connection is created, go to the Settings tab.
- Choose Front Channel or Back Channel as a Type, depending on how you intend to integrate it with your application.
- you should choose Front Channel only if you are developing a pure SPA application. Otherwise, choose Back Channel.
- If you chose Back Channel as a Type, enter the Client Secret generated by Idura Verify when you enabled the OAuth2 Code Flow.
- Select Save Changes.
- Make sure to enable the created connection for your Auth0 application.
After you save a connection, you may get an error: "Error! Something happened while trying to save your connection: Issuer metadata missing the following attributes: token_endpoint".
This is due to a bug in Auth0's frontend, nothing to worry about. In this case, under the Issuer URL select Show Issuer Details and under Token Endpoint enter https://<YOUR COMPANY>.idura.broker/oauth2/token
If you are creating multiple connections, you have to enter Callback URL only once. It will be the same for every OpenID Connect connection.
Test the connection
To test your OpenID Connect connection, go back to the list of all OpenID Connect connections and select Try button on the right side of the connection you want to test. You will need a test user to perform testing.
Custom Social Connection
Alternatively, you can leverage a Custom Social Connection to integrate with Idura Verify via OpenID Connect. Create an OIDC connection for every login method you intend to use.
Create the OIDC connection(s)
- Go to Auth0 dashboard for your tenant and under Authentication choose Social.
- Select Create Connection, go to the bottom of the list, then choose Create Custom.
- Enter Connection name.
- Under Authorization URL, enter a login-method specific authorize URL to which your users will be redirected to log in to your application, e.g.
https://yourdomain.idura.broker/dXJuOmdybjphdXRobjpubzpiYW5raWQ=/oauth2/authorize?scope=openid&client_id=urn:idura:acme-corp:auth0&redirect_uri=https://jwt.io&response_type=code - Under Token URL, enter your token endpoint:
https://yourdomain.idura.broker/oauth2/token - Under Client ID enter the Client ID/Realm from your Idura Verify application.
- Under Client Secret enter the Client Secret generated by Idura Verify when you enabled the OAuth2 Code Flow.
- Add the required Fetch User Profile Script using your
userInfoendpoint, e.g.:
function fetchUserProfile(accessToken, context, callback) {
request.get(
{
url: 'https://yourdomain.idura.broker/oauth2/userinfo',
headers: {
Authorization: 'Bearer ' + accessToken,
},
},
(err, resp, body) => {
if (err) {
return callback(err);
}
if (resp.statusCode !== 200) {
return callback(new Error(body));
}
let bodyParsed;
try {
bodyParsed = JSON.parse(body);
} catch (jsonError) {
return callback(new Error(body));
}
const profile = {
user_id: bodyParsed.uuid,
name: bodyParsed.name,
};
callback(null, profile);
},
);
}
- Create a connection by clicking Create.
- Make sure to enable the created connection for your Auth0 application.
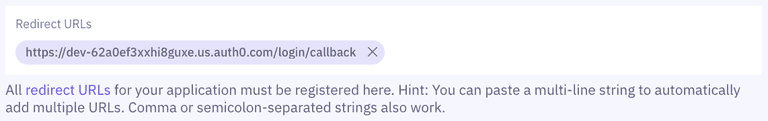
- Lastly, add Auth0's callback URL (
https://{{yourAuth0Domain}}/login/callback) to the Redirect URLs section of your Idura Verify application settings.
Test the connection
Test your Custom Social Connection by clicking the Try Connection button located in the top right corner.
Test users
Most eIDs distinguish between real users and test users.
Real users represent actual individuals who authenticate on your website, providing real personal information such as their name and typically a Social Security Number (SSN).
Test users are fictitious identities used for development and testing. Depending on the eID, you can either create your own test users or use pre-existing ones provided by Idura.
For instructions on creating test users for each eID, please refer to Test user guides.
Integrate your application with Auth0
How to integrate your application with Auth0 depends on the technology you are working with. Refer to the Auth0 quickstart guide for more details.