- Guides & Tools
- Age Verification
Guides & Tools
Age Verification
How to leverage Criipto Verify's Age Verification extension
With the Age Verification extension, you can verify user ages without collecting personal data. The authentication result will simply confirm if the user meets the age requirement, without including sensitive information such as their full name or birthdate.
Age Verification does not require you to set up your own eID provider, as it defaults to using shared Criipto-provided eID providers. This batteries included approach comes with certain limitations, such as the absence of many tenant-specific features.
For instance, the Custom styling feature is not available out of the box for Age Verification applications. To enable it, you can switch to using your own MitID provider.
Prerequisites
You'll need a Criipto tenant and domain to get started.
Create Age Verification application
- On your dashboard, navigate to the Applications tab and click Add application.
- When prompted to choose a product, select Age Verification, then click Create.
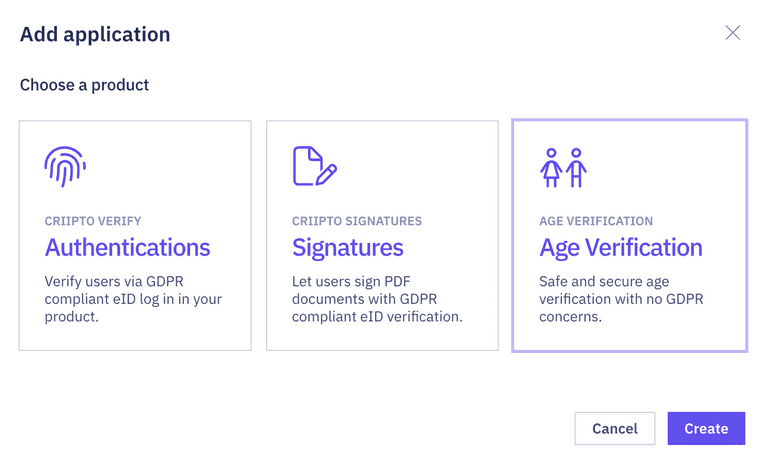
- Fill in the details to create your application, then click Create application.
- You're all set: the Age Verification feature will be automatically enabled after creating the application.
If the Age Verification application type is not available, or you're running into any issues during application creation, please contact us via Slack or by email.
Implementation
Triggering Age Verification
Age verification is triggered via a standard OpenID Connect integration using the following settings:
acr_values=urn:age-verificationlogin_hint=country:{country},{country}can be one ofDK|SE|NO|FI. This determines the eID provider for user authentication.scope=openid is_over_18; Other supported values are:is_over_15,is_over_16,is_over_21.
Example JWT
The resulting JWT will indicate whether the user meets the age requirement. Personal data, such as the user's full name and birthdate, is not included.
The sub field is random for each login and cannot be used to correlate the user.
Authorize URL Builder
General parameters
https://criipto-verify-prod.criipto.id/oauth2/authorize?
scope=openid openid is_over_18&
client_id=urn:criipto:dev&
redirect_uri=https://jwt.io&
response_type=id_token&
response_mode=fragment&
nonce=ecnon-&
acr_values=urn:age-verification&
login_hint=country:DKOptional: use your own MitID service provider
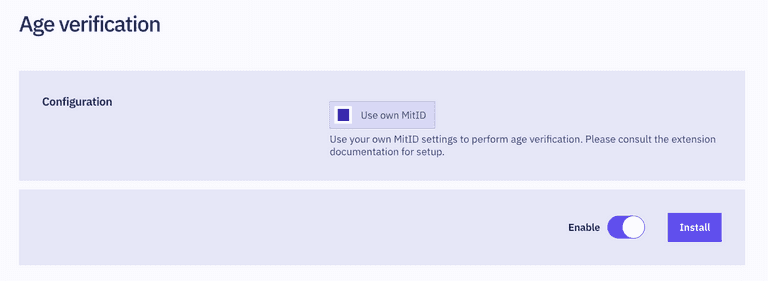
If you prefer to use your own MitID service provider instead of the one provided by Criipto, you have the option to do so.
During installation, flip the Use own MitID setting to enabled, and then ensure that your Criipto application has allowed https://{YOUR_CRIIPTO_DOMAIN}/extensions/ext_ageverification/api/callback as a callback URL.
 Note: You need to apply for MitID production access for Age Verification logins only if using your own MitID service provider.
Note: You need to apply for MitID production access for Age Verification logins only if using your own MitID service provider.
Auditing
Denmark
The id_token is issued in such a way that you can safely store it without worrying about personal data.
The id_token contains a reference to a Criipto managed audit log that contains the users MitID uuid,
upon request an id_token can be presented to Criipto and we can help prove the identity (and thus age) of the user.
For e-commerce scenarios we suggest storing the id_token together with the order.