- eIDs
- Norwegian BankID
eIDs
Norwegian BankID
Learn more about Norwegian BankID token contents, how to create test users and how to gain access to production.
JWT/Token examples
Kodebrikke authenticators
Triggered with acr_values=urn:grn:authn:no:bankid:high (or acr_values=urn:grn:authn:no:bankid)
The level of assurance for these authenticators are: High
The uniqueUserId identifies the legal person corresponding to the login, and is not considered sensitive.
Biometric authenticator (BankID app)
Triggered with acr_values=urn:grn:authn:no:bankid:substantial
The level of assurance for this authenticator is: Substantial
Note that there is no certsubject returned when using Biometrics.
Test users
Creating netcentric test users
Test users are created through the web page at https://ra-preprod.bankidnorge.no/#/search/endUser.
- Go to the "TEST NUMBER GENERATOR" to generate a random, valid SSN.
If you want to test BankID Biometric, please make sure that the "Synthetic" checkbox is unchecked before generating a new number. BankID Biometric app does not currently support synthetic SSN numbers, so you won't be able to use them for testing. - It now says "Could not find any bankIDs for ...".
- Fill out the first name, last name, and BankID friendly name.
- Ensure that
BankID appis enabled in the "HA services" section, if you want to use BankID Biometric. - Click "Order" to initiate the process.
- Click the pencil icon and add a phone number and an email that you want to associate with the test user. You can use any values that match the correct email and phone number formats (note that the number of digits will differ per country). Random values are acceptable as you'll be able to access the one-time codes via URLs, as shown in steps 5 and 11 of the Testing BankID Biometric section.
- Once the process is complete, you will have a test user. User name is the generated SSN, one time password (OTP) is always "otp", and password is always "qwer1234".
It can take up to 1 hour before a newly created test user is activated.
You can test it out at our authentication demo site, which is a small sample hosted by Idura.
Renewing netcentric test users
If you run into issues with test users created earlier (e.g. errors when entering the one time password), your test user certificate might have expired.
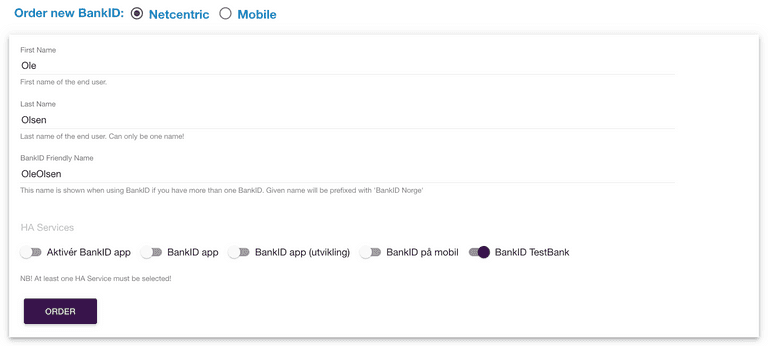
This can be fixed by ordering a new netcentric BankID:
- Find your test user by entering its Personal ID Number number at https://ra-preprod.bankidnorge.no/#/search/endUser
- Fill in the form to order the new netcentric BankID, choosing BankID TestBank in HA Services, and click "Order"
Testing BankID Biometric
Start by creating a netcentric test user as described above.
You will then need to install the test version of the BankID App. Contact our support team to get access to the iOS (distributed via TestFlight) or Android version of the test app. In your request, please provide the email address linked to your Apple ID (for iOS) or your Google account for the Play Store (for Android) used for testing. Our team will get back to you with confirmation and download links for the test app.
The app must be activated before first use:
- Press the Activate BankID app button
- Press the Activate button
- Enter the birth number (SSN) for the test user you created and press the Next button
- Enter the phone number you associated to the test user and press the Next button
- Open the following page to get your your SMS one-time code (after replacing the
yourTestSsnplaceholder with your actual test-SSN): https://toba-preprod.bankidapis.no/test-events/sms-sent-to-qualified-user/yourTestSsn
Note: The page might need to be refreshed several times, and if multiple activations are done in a short period, old SMS codes may be shown. Only the newest activation code will at any point be valid - Type the one-time code that is shown on the website into the app and press the Next button
- Select Alternative activation in the next page
- Press the Get activation codes button
- Proceed past the information pages that explain What you need and the Steps to activate with the chosen method
- Press the Send email button in the "Is this your email?” screen
- Open the following page to get your email activation codes (once again, replace the yourTestSsn placeholder with your test-SSN) https://ra-preprod.bankidnorge.no/notification-console/content/yourTestSsn
- Type the code words that are shown on the website into the app and press the Next button
- Press the Next button in the "Log in using BankID to complete the activation” screen
- Wait until BankID client has loaded in the browser. Pick BankID app in the method list if it is not already preselected.
- Type "qwer1234” as personal password and click the blue arrow button to the right
- A progress bar will appear and when finished you will be activated
- Enable biometrics (which will take you through a flow where you must agree to the terms and conditions)
- Run your first biometrics-based login
Data and consent for Norwegian BankID
Available data / scopes
Basic user information, full name, and date of birth are always made available. Additional data may be requested and is released with explicit user consent only.
For applications configured to use a dynamic scope strategy, the following scope tokens can be supplied: ssn.
| Data type | Released | Verified | scope | login_hint |
|---|---|---|---|---|
| Full name | Always | Yes | ||
| Date of birth | Always | Yes | ||
| SSN ("fødselsnummer" in Norwegian) | User consent | Yes | ssn | scope:ssn |
Example (partial) authorize request with scopes
https://YOUR_SUBDOMAIN.idura.broker/oauth2/authorize?scope=openid ssn&...
Alternatively, you can send them in the login_hint
https://YOUR_SUBDOMAIN.idura.broker/oauth2/authorize?...&login_hint=scope:ssn&...
which can be a useful if you are working with technology that does not let you control the scope value.
Access to the SSN is governed by Norwegian law, as described in the Ordering Norwegian BankID guide.
The unverified data are supplied by end-users and not verified by Bidbax (operator of BankID) or the Norwegian banks.
Consent model
End-users must explicitly grant consent to releasing the data to you.
The consent model is enforced by Bidbax, and they also provide the consent and data collection dialogs.
If you choose the consent model Already granted, you are responsible for obtaining consent from your end-users before they go through the login flow.
Forced and optional consent
If you request SSN, it will be treated as a required value. End users will not be allowed to complete a login until they have explicitly given their consent to release SSN.
All other additional data are treated as optional values. A login may complete even if the user does not consent to release the requested data.
Consent to SSN will be stored by Idura for 1 year for your tenant, after which the user must provide explicit SSN consent again.
Idura does not store the SSN itself, just the fact that the user has granted your tenant access to it.
You can add a "forget-me" link on your website if you want to let users revoke the consent again. Use a normal authorize request as target, but add a prompt=consent_revoke query parameter to the request. Idura will then run a login flow (to be able to recognize the end user), and delete the granted consent.
You can learn more about authorize requests in our authorize URL builder.
Configuration
You can use the Idura Dashboard to configure access to the optional user data, in the Identity Sources -> NO BankID section.
Signing text
Norwegian BankID supports signing text.
Text signing is triggered by using the action and message parameters via login_hint.
- The
actionparameter must be set tosign - The
messageparameter must be base64 encoded.
Note: Signing produces very large JWTs that are not appropriate for authentication/Bearer header use
Text signing has a different eID cost than authentication, please contact Idura sales if you have questions.
Example
login_hint=action:sign message:VmVuZG9yOgoKQ29vbCBEZWxpdmVyeQoKQW1vdW50OgoKMzAwIEVVUgoKCgpJIGFwcHJvdmUgdGhpcyB0cmFuc2FjdGlvbi4=
Try out the example in our URL builder
Ordering Norwegian BankID
To start accepting real users with Norwegian BankID, you must first request your client credentials from Bidbax. The credentials consists of a client id and a client secret.
Prerequisites for ordering
In order to apply for the BankID client credentials for a company you must meet the basic requirements:
- Your company must be a customer of a Norwegian Bank. Most banks in Norway are part of the BankID network.
- The person that will sign the contract must be in possession of one of these personal eIDs: Norwegian BankID, Swedish BankID, or Danish MitID.
- You must have completed step 5 in the Getting ready for production guide. You will need the production domain to complete the order for your client credentials.
New customers
The BankID OIDC Biometrics option is now available when ordering BankID.
Biometrics is always included in the basis agreement.
Existing customers
Due to new terms and conditions in the agreement, you must send us an updated application if you wish to use BankID Biometrics.
BankID Biometrics assurance level
BankID Biometrics assurance level is “Substantial”.
Learn more about assurance levels.
If you can only use assurance level “High” in your login flow, you must explicitly specify the login_hint=BID in your authorize requests to Idura Verify. Please note that using login_hint=BID will disable biometrics in the BankID app.
Modifying user flows
By default, the user flow is controlled by the user-defined settings of the BankID app: no additional configurations required. If necessary, you can adjust the user flow by adding a login_hint to the authorize URL.
The table below provides a list of options for using login_hint with Norwegian BankID, and the resulting user flows. Check our guide on prefilled fields to learn more.
| Parameter name | Description |
|---|---|
login_hint=BID | The user will be redirected to the BankID app, with biometrics disabled. The user will be queried for userID(i.e. national identity number) in the first dialogue. |
login_hint=BID:[SSN], where [SSN] has the format DDMMYYXXXXX | The user will be redirected to the BankID app (with biometrics disabled) along with a pre-selected userID. The userID dialogue is omitted in this case. |
login_hint=BIS | The user will be redirected to the BankID app. The user will be queried for userID in the first dialogue. This option does not disable biometrics. |
login_hint=BIS:[SSN], where [SSN] has the format DDMMYYXXXXX | The user will be redirected to the BankID app with a pre-selected userID. This option does not disable biometrics. |
no login_hint provided | The default settings of the BankID app on the user's device will determine the flow (whether biometrics are enabled or disabled). |
Ordering the client credentials
To order production credentials please send a request to
with answers to these questions:
- A short description of what your application does and why it needs BankID.
- Your company: Name, organisation number, and address.
- General contact person at your company for BankID related communication: Name, mobile phone, and email.
- Person registered in the business registry with authorization to sign the agreement: Name, mobile phone and email.
- Your company’s Norwegian bank: Name, organisation number, and address.
- Contact person with authorization to receive the client credentials and client secret: Name, mobile phone, and email.
- Contact person with authorization to block/revoke the use of BankID: Name, mobile phone, and email.
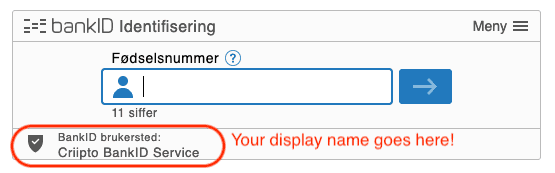
- The display name to appear in the login app. E.g. the name of your company or your specific service (see the image below).
- The URL of your Idura Verify production domain as setup in step 4 of the Getting ready for production guide.
- If you need access to social security numbers (“fødselsnummer”) please provide a thorough explanation of why and reference the Norwegian law and paragraph that grants you the right to receive them. If SSN is needed, then the reference to the Norwegian Law and Paragraph is mandatory.
- Finally - if you are not a Norwegian company - you must enclose a company certificate from the official business registry of the country of incoporation.
Next steps
After Idura has received the above information, we order the client credntials from your bank by filling out an online agreement, which is then sent to the appointed persons at your company for signing. Idura will also sign the agreement.
When all signatures are in place the signed agreement is sent to your bank for further processing and eventual issuance of your client credentials.
Once you have received credentials, they must be entered into the Idura Verify management UI to configure your NO BankID integration.